Hi everyone,
We have a new feature in the acs-admin posture-overview page (/acs-admin/posture-overview): In addition to the existing privacy and privilege analyses and JavaScript library checks, the overview now also displays known CVEs for:
- Database client libraries (e.g. libpq via the "nsdbpg" driver)
- Database servers (PostgreSQL, etc.)
If your installation is using an affected version, you’ll see advisories right alongside the other vulnerability alerts (see below).
How It Works:
- Version Fetching: The NaviServer–nsdb API was extended with a "versionProc" callback. The "nsdbpg" driver uses this to report its client version and the connected server’s version.
- Database-Agnostic Interface: Although today only "nsdbpg" returns version info, any other database driver can implement its own "versionProc" hook—no changes to the NaviServer core required.
- Vulnerability Lookup: Once we know the versions, we cross-reference them against a curated list of database CVEs and surface any matches.
To enable this feature, simply upgrade to the latest releases of:
- NaviServer (with the new "versionProc" API, included in the forthcoming release of NaviServer 5)
- nsdbpg (v2.9+)
- acs-admin and acs-tcl from the oacs-head branch
If either component is out of date, the new “Database Vulnerability Check” section will be omitted.
Example
This screenshot show an output example for PostgreSQL version 13.4 in the client library (used for linking nsdbpg) and 14.10 as database server:
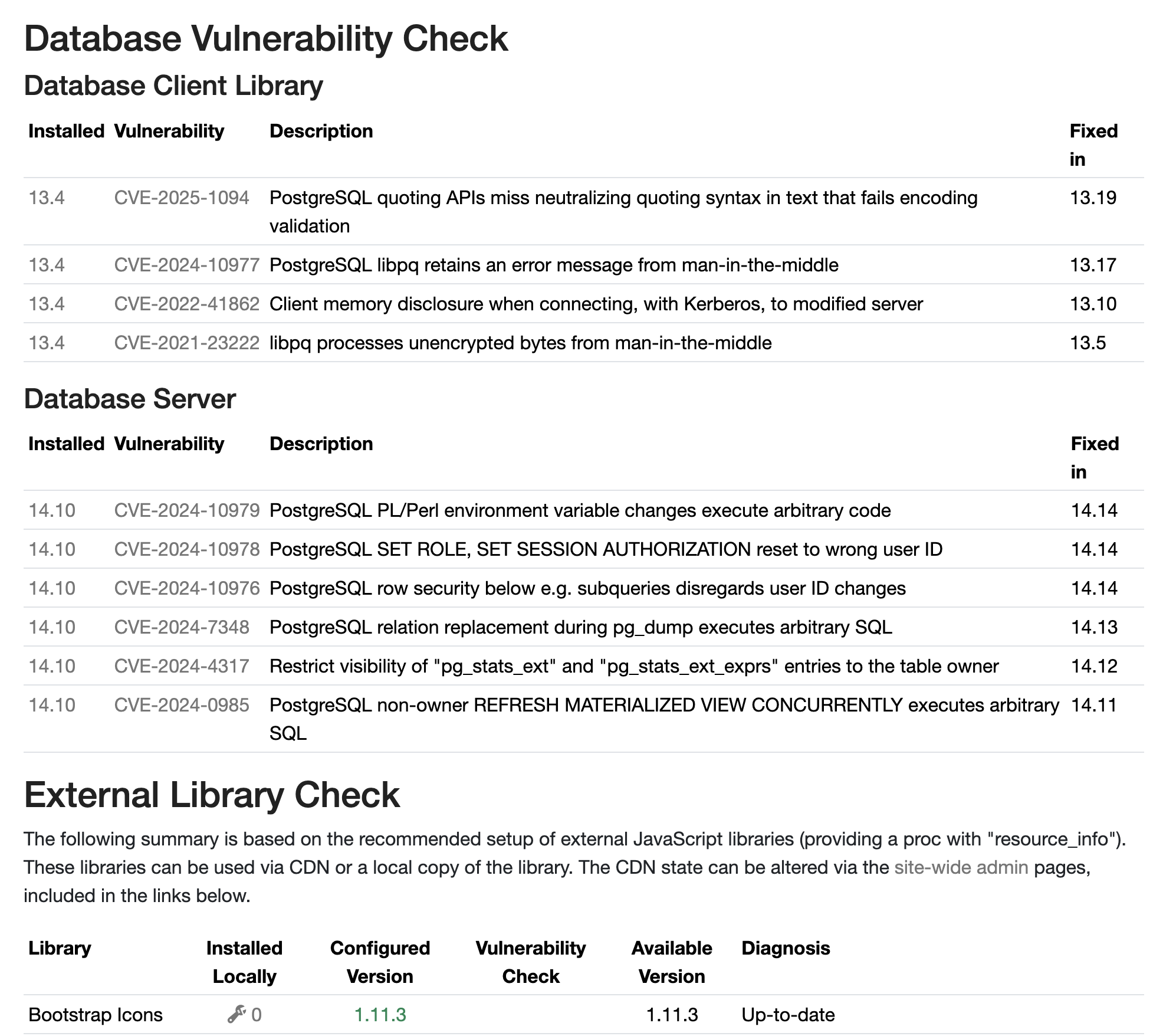
This new feature has the goal to make the life of OpenACS administrators easier and provide motivation for upgrades. All this information was available in other ways, but as reality shows, people use often outdated versions without knowing the potential implications. Making vulnerability information easy accessible should improve overall security.
All the best
-g